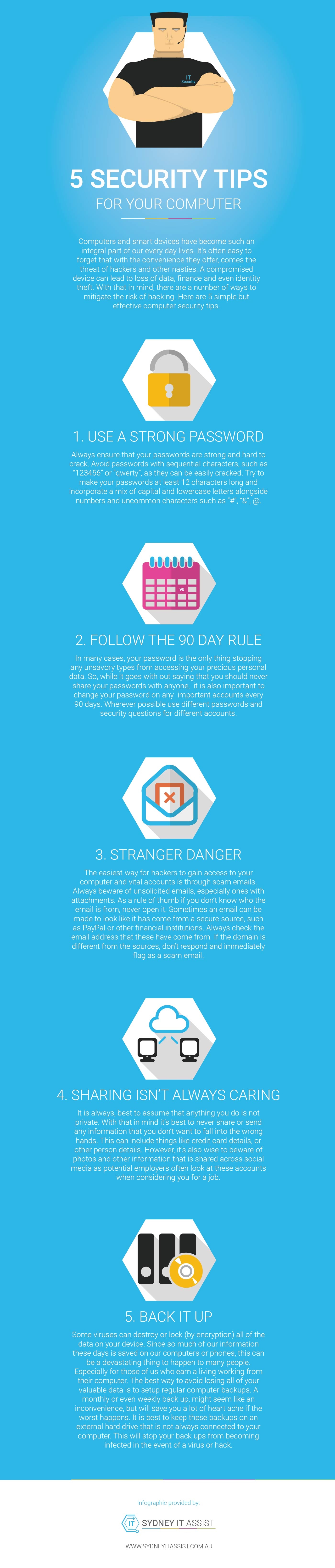
Computers and smart devices have become such an integral part of our every day lives. It’s often easy to forget that with the convenience they offer, comes the threat of hackers and other nasties. A compromised device can lead to loss of data, finance and even identity theft.
With that in mind, there are a number of ways to mitigate the risk of hacking. Here are 5 simple but effective computer security tips that Sydney IT Assist would like to share with you.
Please copy the code below to share this image on your Site
“5 Security Tips for your computer” Infographic Transcription
Computers and smart devices have become such an integral part of our every day lives. It’s often easy to forget that with the convenience they offer, comes the threat of hackers and other nasties. A compromised device can lead to loss of data, finance and even identity theft. With that in mind, there are a number of ways to mitigate the risk of hacking. Here are 5 simple but effective computer security tips.
1. USE A STRONG PASSWORD
Always ensure that your passwords are strong and hard to crack. Avoid passwords with sequential characters, such as “123456” or “qwerty”, as they can be easily cracked. Try to make your passwords at least 12 characters long and incorporate a mix of capital and lowercase letters alongside numbers and uncommon characters such as “#”, “&”, @.
Learn more about password management tools
2. FOLLOW THE 90 DAY RULE
In many cases, your password is the only thing stopping any unsavory types from accessing your precious personal data. So, while it goes with out saying that you should never share your passwords with anyone, it is also important to change your password on any important accounts every 90 days. Wherever possible use different passwords and security questions for different accounts.
3. STRANGER DANGER
The easiest way for hackers to gain access to your computer and vital accounts is through scam emails. Always beware of unsolicited emails, especially ones with attachments. As a rule of thumb if you don’t know who the email is from, never open it. Sometimes an email can be made to look like it has come from a secure source, such as PayPal or other financial institutions. Always check the email address that these have come from. If the domain is different from the sources, don’t respond and immediately flag as a scam email.
4. SHARING ISN’T ALWAYS CARING
It is always, best to assume that anything you do is not private. With that in mind it’s best to never share or send any information that you don’t want to fall into the wrong hands. This can include things like credit card details, or other person details. However, it’s also wise to beware of photos and other information that is shared across social media as potential employers often look at these accounts when considering you for a job.
5. BACK IT UP
Some viruses can destroy or lock (by encryption) all of the data on your device. Since so much of our information these days is saved on our computers or phones, this can be a devastating thing to happen to many people. Especially for those of us who earn a living working from their computer. The best way to avoid losing all of your valuable data is to setup regular computer backups. A monthly or even weekly back up, might seem like an inconvenience, but will save you a lot of heart ache if the worst happens. It is best to keep these backups on an external hard drive that is not always connected to your computer. This will stop your back ups from becoming infected in the event of a virus or hack.
If you suspect your computer or device is infected immediately contact your local IT company, for computer repairs in Sydney, we have you covered.






 Good old DVDs are just a disk with huge amounts of data stored as 1s and 0s in a particular format. The DVD player reads this data, decodes it into a video file and sends it to the TV screen.
Good old DVDs are just a disk with huge amounts of data stored as 1s and 0s in a particular format. The DVD player reads this data, decodes it into a video file and sends it to the TV screen.
 There are certain myths that circulate about computer repair that, once told often enough, people start to believe.
There are certain myths that circulate about computer repair that, once told often enough, people start to believe.